Kangyeon Lee
Cybersecurity
Network Engineering Technology
Undergraduate @ Purdue University
Designing Enterprise Network Solution
Objectives
This project focused on designing enterprise networks separating the network into WAN, DMZ, and LAN to enhance the security of the corporate network and manage the network more effectively. The implementation was done virtually using VMware vSphere.
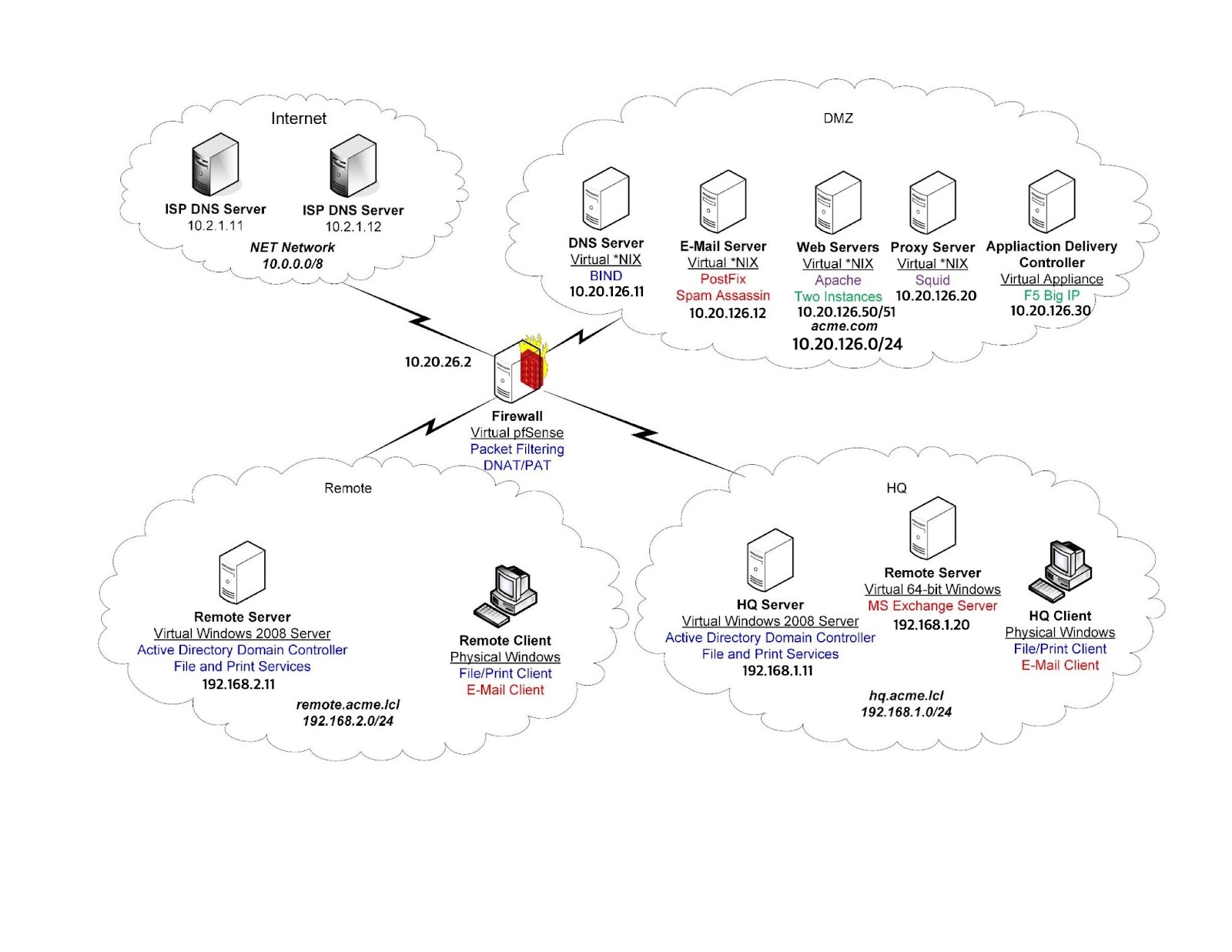
Design Diagram
pfSense was deployed in the center of three different zones: Remote, HQ, and DMZ. Remote and HQ are two different internal zones and DMZ zone was created to act as a access vestibule between external and internal network.
Windows Services
To efficiently manage enterprise users with windows desktops, Windows Actie Directory service was deployed. Internal DNS server was deployed to increase reliability and create locacl zones.
DMZ DNS Server
Another DNS Server was deployed in the DMZ zone to provide external and internet DNS services to corporate users. BIND DNS server was deployed on a linux machine.
With the deployment of a DMZ DNS server, the internal DNS server configured on internal Windows Servers was configured to forward DNS request to the DMZ DNS Server.
Mail Server
DMZ
In order to accept emails from the public network, a PostFix mail relay server was deployed. In addition to that, SpammAssassin SPAM filter was also placed in the DMZ zone to filter out SPAM Emails.
Internal
In the internal network, Microsoft Exchange Server was deployed to function as an internal mail server.
Web Server
Apache
Two instances of apache web server were deployed. The reason for deploying two identical instances of the web server is to allow load-balancing web server traffic.
F5 Big-IP LTM
F5 Big-IP LTM was deployed to function as a load balancer.